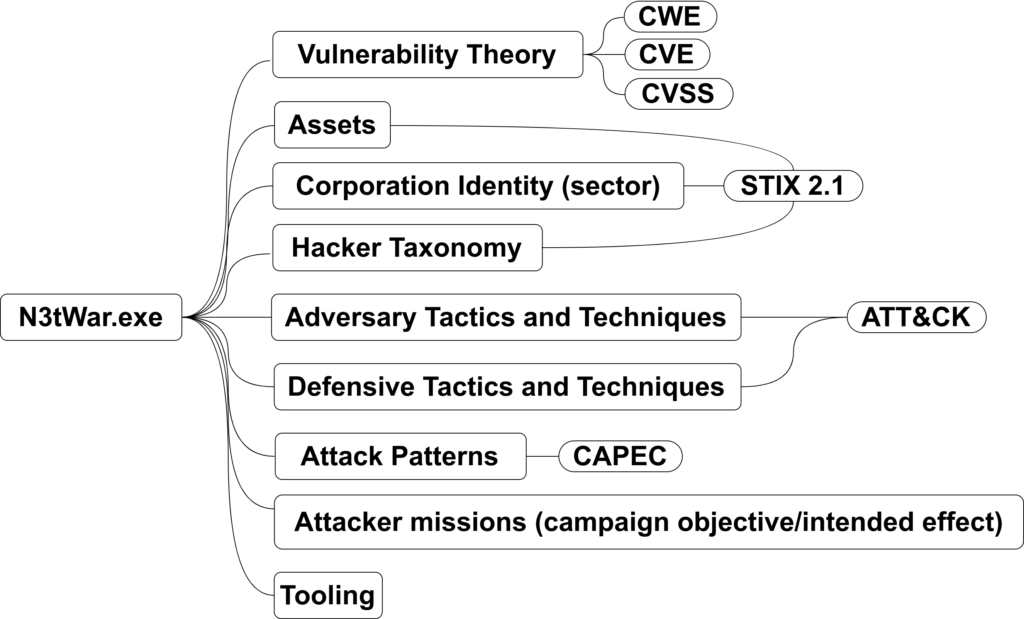
For the most part, the game has been structured around the learning objectives of the Ethical Hacking part of the IMT3004 joint course. The most relevant learning objectives for this introductory course are related to the stages of pentesting & red teaming, vulnerability theory, vocabulary, hacker taxonomy, offensive & defensive techniques and tooling.
This has been realized by incorporating into the game the most common standards that play a role in a cyber security ecosystem.
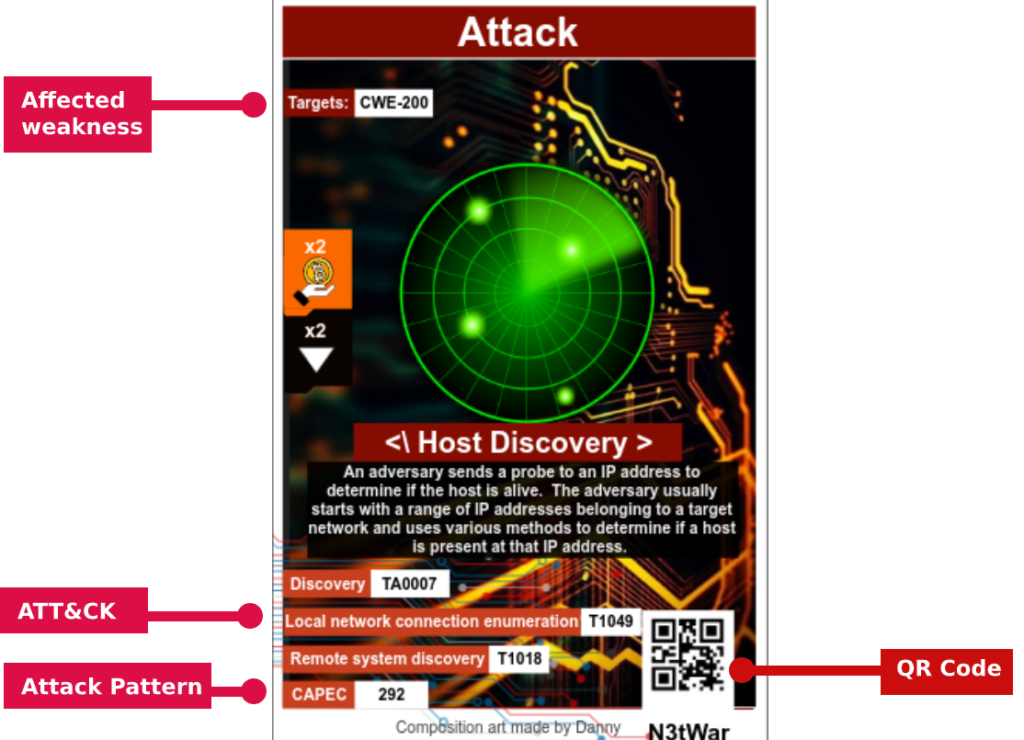
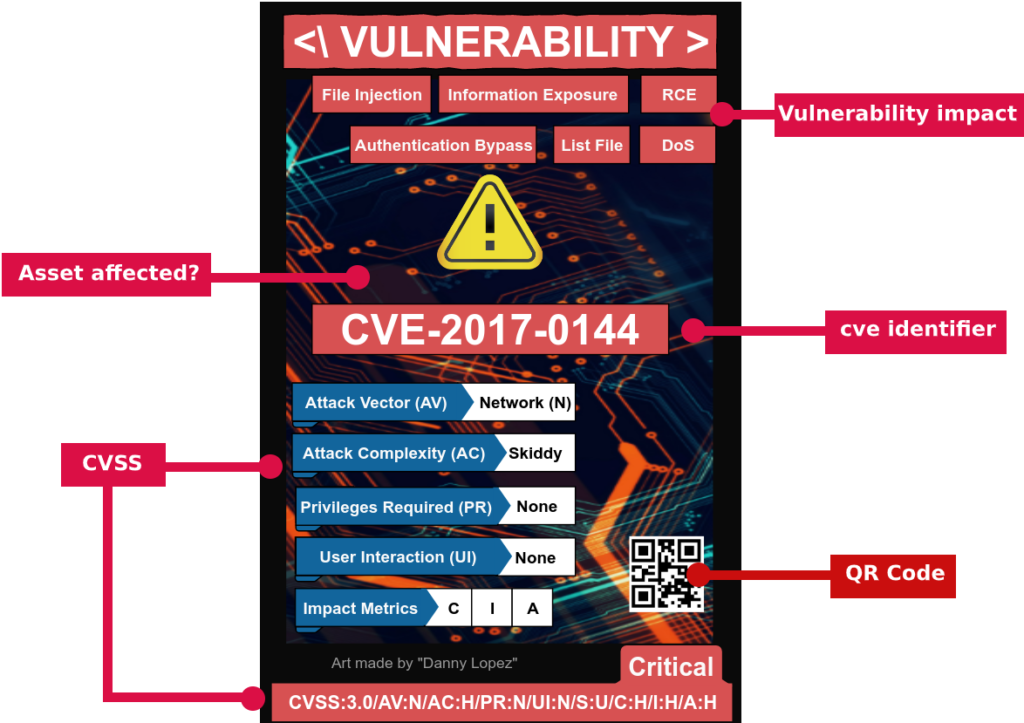
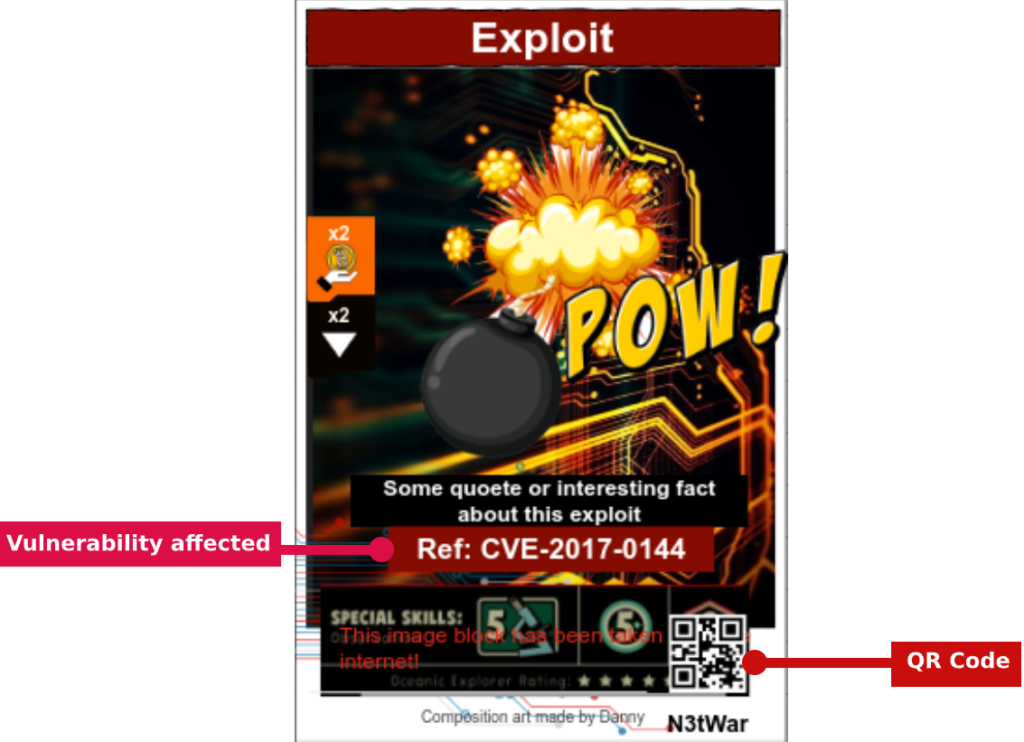
Most game elements highlighted in the image below such as CVE, CWE Mitre ATT&CK/UKC(?), have been directly embedded in the card design.
Hacker taxonomy backgroun story and direclty in the card
Each player’s roles were ascribed mechanics that are representative for the type of hacker they represen
The dictionaries CVE and CWE and the vulnerability scoring system CVSS have been directly incorporated in the card design of the vulnerabilitiy cards
When appropriated, a mapping between ATt&CK and CAPEC is done….
Real live objectives/campaigns: expose companies dark agendas. One example of such agendas are: UNIT 180 or UNIT 120.
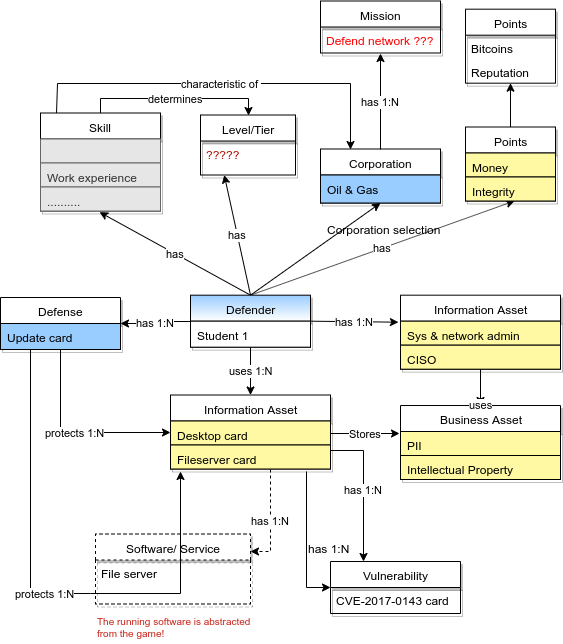
All defender concepts:…
All attacker concepts:…
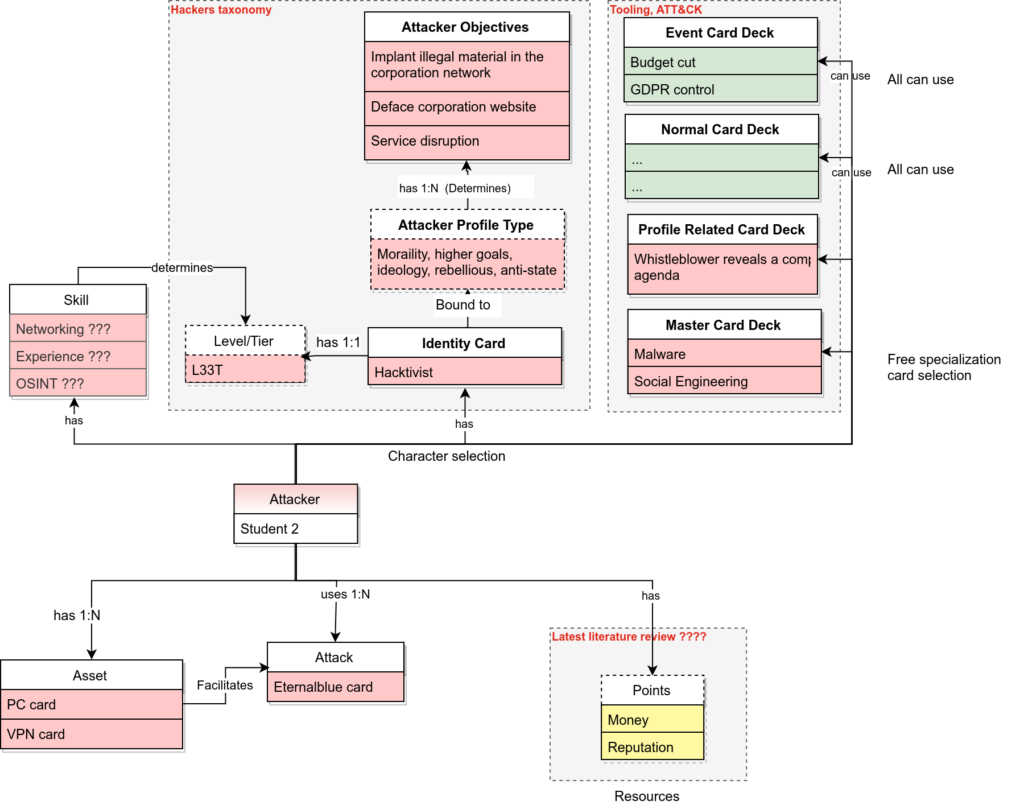
…work in progress…