Goal
Intrusion Attempt is a is a multiplayer asymmetric turn based expnadable card game with Standardized Expansion Packs where students assume the role of hackers (attackers) and corporations (defenders). The game has been envisioned as an informal supplementary tool that can be used by educators who want to convey real-world cyber attacks and defense techniques to (under)graduate students, teach about cyber crime, adversary thinking and promote security awareness in an entertaining way!
The asymmetric nature of the game and some of the game mechanics implemented in Intrusion Attempt have been influenced by games such as Android NetRunner, a discontinued collectible card game with a large fan base that takes place in a dystopian cyberpunk futuristic setup where hackers try to steal the agendas of mega-corporations.
…..[Work in progress]
Intrusion Attempt can be played in two different modes, multiplayer single-mode and multiplayer cooperative mode:
- Multiplayer single mode: in multiplayer single mode, each student selects a single role to play, namely a hacker role or a corporation role. The minimum number of participants for multiplayer single mode is two (2) (I.e. two-player mode). In two-player mode, one player selects the role of a hacker, while the other selects the role of a corporation.
For more than two (2) participants, the ratio of hackers to corporation is 1 to 2 and the recommended maximum number of participants is five (5). - Multiplayer cooperative mode: in multiplayer cooperative mode, students are allowed to play in teams no larger than two (2) participants per team. The maximum recommended number of teams is four (4).
…a bit of history
I have been working since 2017 at NTNU as research assistant for the Norwegian Cyber Range project and as a lecturer for the Ethical Hacking part of a join course called Incident Response, Ethical Hacking and Forensics (IMT3004). The penetration testing part of the IMT3004 course has a theoretical and practical approach that aims to teach students the most common techniques, methodologies and tactics used by malicious adversaries to compromise computer systems.
The course is not only popular among students with strong technical skill and abilities related to cybersecurity, it also attracts less experience students, many of which have never participated in a CTF before but are interested in understanding the technical details behind cyberattacks and may be considering pursuing a position as junior penetration testers or an executive function in cyber security.
One of the biggest challenges I faced (like most educators face in this field of expertise) is the disparity in the level of readiness and technical knowledge among the students that take the course for the first time.
The complexity of the topic, the difference in background and experiences among the students that take the course, makes teaching such a course very challenging. If this issue is left unaddressed, the level of demotivation among novice participants can grow larger as the challenges they face throughout the course will only grow in difficulty. This could eventually lead to unwanted results such as, bad scores, cheating and group collaboration when it is not allowed and a potential decline of interest of some of the novice students for the field.
Unfortunately, given the large amount of students that are allowed to take part int he course (i.e. 50+ students), it is in most cases not always possible to provide dedicated assistance to those students who are lagging behind.
One of the solutions I was eager to explore in an attempt to make the course content more engaging, more accessible and to allow students to learn without the fear of grading and judgment, was to incorporate an educative game in the classroom. To my dissatisfaction and disappointment, and even though there have been plenty of cyber security oriented games, many of them were not relevant for the course I was teaching. And those that were, did not fulfilled the objectives of the course. That is why I decided to create Intrusion Attempt.
Why a card game?
A cad game seemed very appropriate since it allows me to adjust the game to make sure that it always states true to the subject I want to gamify. This is realized by the creation of new cards and by retiring obsolete ones when needed. On top of that, the adapting/evolving nature of the game, the different options players have, and the random elements incorporated into it (in the form of e.g. event cards and dices), contributes to the uniqueness of each game play.
What is new?
Intrusion Attempt intends to differentiate itself from many card games that have been developed with a related purpose in mind by trying to achieve a level of realism that other games do not, focusing mostly on the technical side of attack and defense strategies and adversarial thinking. This make the game suitable for teaching penetration testing and red teaming.
Intrusion Attempt is meant to evolve along side with the technological advanced within this field, making it always relevant for teaching real-world offensive and defensive techniques to a mature audience.
The level of realism in Intrusion Attempt is achieved through the following elements:
1) Less abstraction
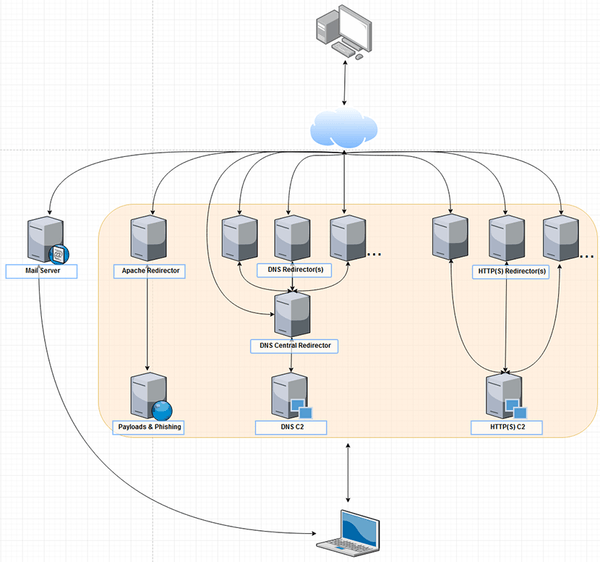
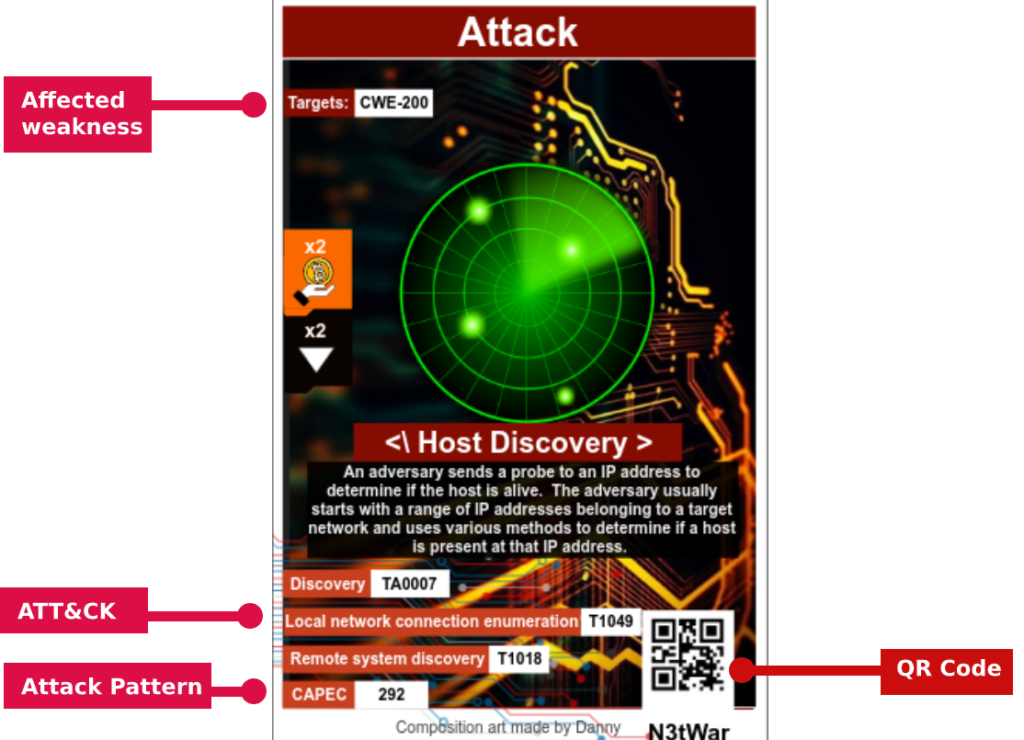
Abstraction plays an important role in most cyber security card games. Many key elements and concepts that are part of an attack are assumed to exists and are therefore abstracted away from the player, often in the form of a single card. This does of course favor game complexity, but it does not favor the learning process of the students.
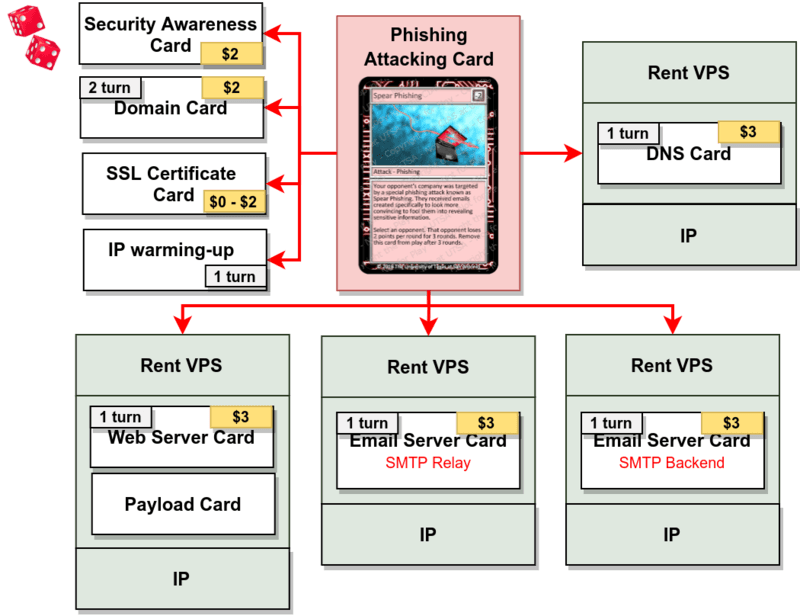
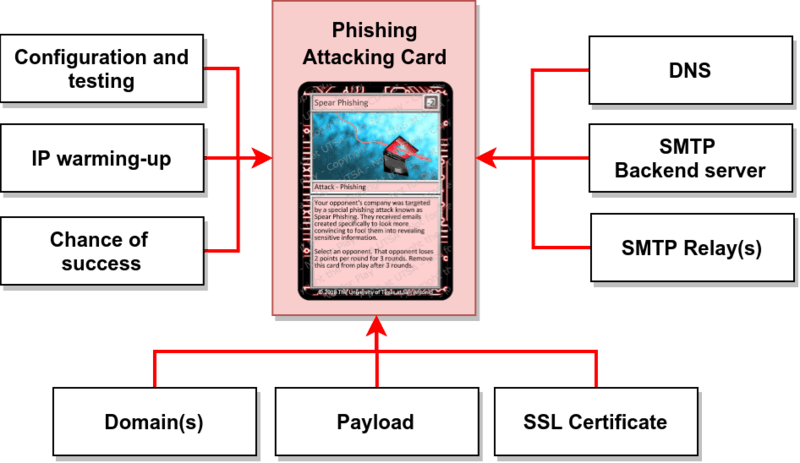
Intrusion Attempt does not abstract away important key elements from the players, they are instead playable cards that when combined together can form powerful attacks!
3) Hacker Profiles
….
4) Cyber crime schemes, behaviors & DNM
The cards featured in the game have been designed to provide students with a good overview into real cyber crime activities (e.g. Business Email/Process Compromise, money mules, underground banking, corporate espionage and honey traps), generate insights into the complex world of cyber security and encourage communication, team work and understanding of the subject matter.
…….The Darknet Market (DNM) and DNM specific cards such as Escrow and Mutltisig, play an important role in the game!
…understanding cybercrime is important to be able to understand malicious actors, that is why cybercrime is included, this will make better pentesters/red teamers.
5) Interactive app & knowledge base
……
…work in progress…