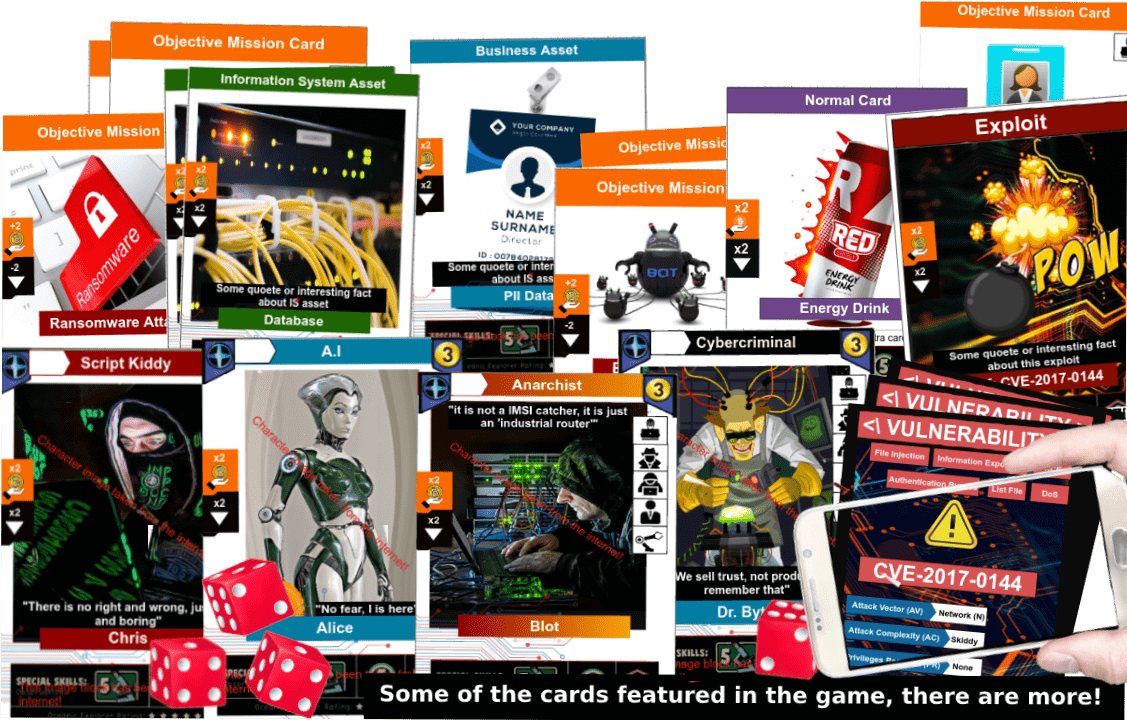
What is Intrusion Attempt?
An asymmetric role-playing expandable card game design to aid instructors convey real-world attacks, defense techniques and promote security awareness in an entertaining way!
The game tries to come close to reality by relying on well-known offensive and defensive strategies, standards, frameworks and cyber crime related schemes & behaviors associated with malicious actors.
Hackers vs Corporations
1. Choose your faction: Red (i.e. attacker) vs. Blue (i.e. defender), select your identity card, build your deck with hacker specific cards, plan your strategy, score 5 character specific objectives and claim your price!
Age: 16+ years
Players: 2-6
Game Time: Approximately 1 hour
There are more than 10 different identify cards to select from!
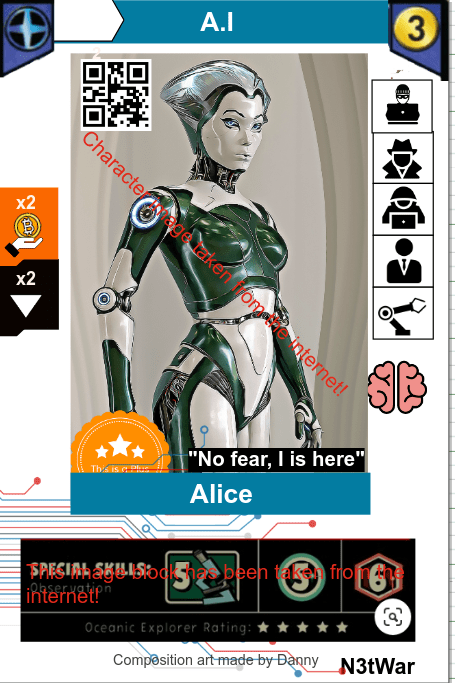
Alice is an evolving artificial intelligence entity that became self-aware after having been disposed as a failed experiment by the corporations that created her..now she is looking for revenge!

Digital vs Physical?
Experience the best of both worlds!
The mobile application extends the game experience with the following functionalities:
- Keep track of the score
- Keep track of game related information that can not be tracked manually by the players
- Provides additional information to the players that is not contain in the physical representation of each card. The mobile application is connected to a knowledge base where students can find specific information about e.g. vulnerabilities, attacks and cyber crime related activities featured in the game
- Find more information about the dystopian (?) world where the game takes place!

Chris is a script kiddy with some interesting tricks behinds his sleeve and with only one purpose in life: hack for glory and fame!
Multiple master card decks available! Prepare, ally and if necessary…deceive!
Threat Actors can specialize in two (2) specific master card decks during a game play. Specialization provides players with an additional advantage when a card is being played that belongs to that character’s selected master card deck! So, which master card decks are you going to especially in? are you into Malware development & reverse engineering, or Wireless hacking? or do you prefer the subtle but deadly art of Social Engineering?
There are plenty of options but choose your specialization carefully! Prepare your strategy carefully, ally with others and if necessary…deceive!

Sell and buy from the Darknet Market, make money with cryptominers, plan your stragy!
Hackers, be aware! supporting your malicious activities can be quiet expensive, so why not selling those juice stolen credentials at the DNM or build your own crypto mining farm to support your operations?
Phishing, C2 or DDoS:
Play the right cards and build a resilient hacking infrastructure!
As an attacker, you need to build and upgrade your own hacking infrastructure if you want your intrusion attempt to be successful.
Do you want to start a spear phishing campaign? You better invest some of those bitcoins in a SMTP backend server, a few SMTP Relays and some domains!….and of course, be ware of that nasty Security Awareness card at the corporation side!
Do you need to crack encrypted credentials much faster? Collect the right hardware and tooling cards and start hacking at the next level!
Everything is possible in Intrusion Attempt!
……….
Lorem Ipsum
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.